Generative AI is no longer a futuristic concept; it’s a transformative force that businesses are eager to harness. But as Large Language Models (LLMs) like GPT become more powerful, a critical question looms for every executive and IT leader: “How can we leverage this technology with our proprietary data without putting our sensitive information at risk?” Many are finding the answer in a powerful and increasingly popular architecture: Retrieval Augmented Generation (RAG).
For businesses, the fear of data vulnerability is real. Concerns about data privacy, cyber threats, and employees making decisions based on inaccurate information are significant barriers to AI adoption. RAG offers a robust framework that acts as a secure intermediary between your internal knowledge and the powerful reasoning of LLMs, delivering accurate, context-aware responses while keeping your data safe. The Problem with Pouring Your Data Directly into an LLM.
Developers train standard LLMs on vast amounts of public data. To make them truly useful for your business, they need access to your internal documents, databases, and institutional knowledge. The traditional approach might be to “fine-tune” a model by training it on your private data. However, this method comes with significant security risks:
Data Leakage: Once a model provider uses your data for training, it becomes part of the model’s “knowledge.” This increases the risk of sensitive information being inadvertently exposed in responses to other queries.
Lack of Control: You hand over your proprietary data to the model provider, which reduces your control over its use and storage.
Hallucinations: LLMs can sometimes generate plausible but incorrect information, a phenomenon known as hallucination. When dealing with business-critical data, this can lead to costly errors and misinformation.
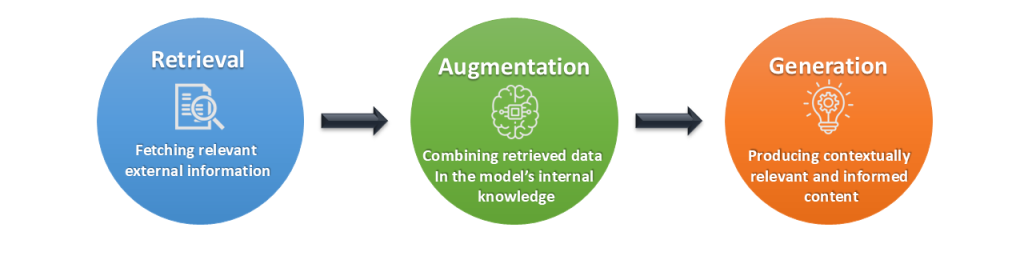
Retrieval Augmented Generation fundamentally changes the game. Instead of retraining the entire model, RAG connects the LLM to your company’s knowledge base in real-time. Think of it like an open-book exam. The LLM is a brilliant student, but instead of relying solely on its memory (pre-trained data), it can look up the correct information from approved company data before answering a question.
This process happens in two main stages:
Retrieval: When a user asks a question, the RAG system first searches a secure, external knowledge base, like your company’s internal documents or databases, for relevant information.
Generation: The RAG system then packages this retrieved information with the original query and sends it to the LLM as context. The LLM uses this fresh, accurate information to generate a relevant and fact-based response.
This simple but powerful architecture provides several layers of security that directly address the concerns of businesses.
The true beauty of RAG lies in its ability to provide both intelligence and security. Here’s how it creates a more secure environment for your data:

Your Data Stays Yours
With RAG, you don’t have to store your sensitive, proprietary data within the LLM. It remains in your own secure environment, such as a vector database. The model queries this database in real-time to fetch the necessary information for a specific task, significantly reducing the risk of data leaks. This approach allows businesses to process data internally and ensure only the intended information is transmitted.
Granular Access Control
A critical vulnerability in many systems is the lack of robust access controls. RAG architectures can be designed to enforce user permissions at the retrieval step. This means the system can filter information based on the user’s role and permissions before it ever reaches the LLM. Whether you use Role-Based Access Control (RBAC), Relationship-Based Access Control (ReBAC), or Attribute-Based Access Control (ABAC), RAG ensures that users can only see the data they are authorized to view, preventing inadvertent exposure of sensitive information.
Grounded in Truth, Not Hallucinations
By grounding the LLM’s responses in specific, verifiable documents from your own knowledge base, RAG dramatically reduces the risk of hallucinations. This is a crucial security feature, as it prevents the dissemination of misinformation that could lead to poor business decisions. The system can provide precise, verifiable answers based on your actual business information, and even cite the sources used to generate the response, adding a layer of transparency and trust.
Robust Data Governance and Compliance
Effective data governance is foundational to building trustworthy and compliant AI applications. RAG systems facilitate better governance by providing a clear framework for managing your knowledge base, user queries, and the responses generated by the LLM. This includes ensuring the quality and timeliness of the source data and providing auditable trails for how information is used. This is particularly crucial for industries like healthcare and finance that handle highly sensitive data.
While RAG offers substantial security benefits, it’s essential to recognize that it also introduces new considerations. The vector databases that store your indexed data can become a target, and risks like “RAG poisoning”, where malicious data is inserted into the knowledge base, need to be mitigated.
To build a truly secure RAG system, businesses must adopt a multi-layered security approach, including:
Data Encryption: Both in transit and at rest, especially for the vector database.
PII Redaction: Automatically detecting and masking personally identifiable information (PII).
Input Validation: To protect against prompt injection and other malicious inputs.
Regular Monitoring and Auditing: To track data access and system behavior.
For businesses looking to embrace the power of generative AI without compromising on security, Retrieval-Augmented Generation offers a clear and compelling path forward. By keeping your data within your control, enforcing strict access permissions, and grounding AI responses in fact, RAG allows you to build powerful, reliable, and trustworthy AI applications. It transforms the promise of AI into a practical and secure reality for the modern enterprise.